Monte Carlo is SOC 2 Certified

When it comes to managing your company’s data, security is high on your list of priorities.
Today, I’m thrilled to share that Monte Carlo has achieved SOC 2 Type I certification, an industry-leading standard for the security, availability, and confidentiality that our organization adopted.
What does this mean for you?
Our SOC 2 designation means that Monte Carlo has designed a set of internal controls, systems, policies, and procedures that meet industry best practices for protecting our customer data. This certification also verifies that our service meets the highest availability standards, reinforcing our commitment to providing a high quality solution to our customers. After all, any solution dedicated to keeping data pipelines reliable should take its own medicine when it comes to building the actual product.
Many of our customers have adopted SOC 2 as a standard for their own security and compliance, and many of the best security teams consider SOC 2 to be a preferred or often required certification for software vendors. As part of our mission to help as many data teams as possible avoid data downtime, it was obvious to us that we needed to match or exceed our customers’ security posture. We are thrilled to reach this milestone and increase confidence in our security as we help make data more trustworthy and reliable.
If you want to learn more about what SOC 2 certification means for you, check out this comprehensive list from InfoSecurity Magazine.
Monte Carlo’s commitment to your data’s security and privacy
Before we even founded Monte Carlo, we knew that security and compliance would be front and center when it came to building our data observability platform architecture. In fact, security runs in our DNA, with several us Monte Carloians hailing from cybersecurity providers like Barracuda and a few of us having patented machine learning systems to prevent email phishing attacks.
Specifically, with Monte Carlo, data never leaves your environment — full stop. We designed our product without having to store or access individual records, PII, or any other sensitive information. Instead, we only extract query logs, metadata, and aggregated statistics about data usage to ensure that your most critical data assets are as trustworthy and reliable as possible.
Under the hood, we use read-only access via APIs and/or dedicated service accounts to access this metadata, enabling granular permissions to datasets of your choice. Our hybrid architecture allows you to run our collectors on your own cloud infrastructure so you never have to expose any of your data warehouses, data lakes, and business intelligence tools to our cloud. And this only scratches the surface of our commitment to our customers’ security and privacy.
What’s next?
In future blog articles, we’ll discuss our approach to building our security-first data observability platform and share best practices for meeting data reliability requirements for the modern data stack.
Until then, here’s wishing you no data downtime!
Interested in learning more about Monte Carlo’s approach to security? Reach out to Itay and the rest of the team.
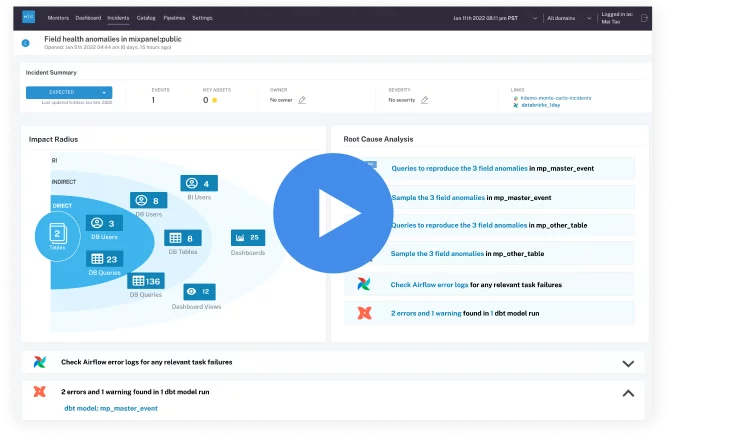 Product demo.
Product demo.  3 Steps to AI-Ready Data
3 Steps to AI-Ready Data 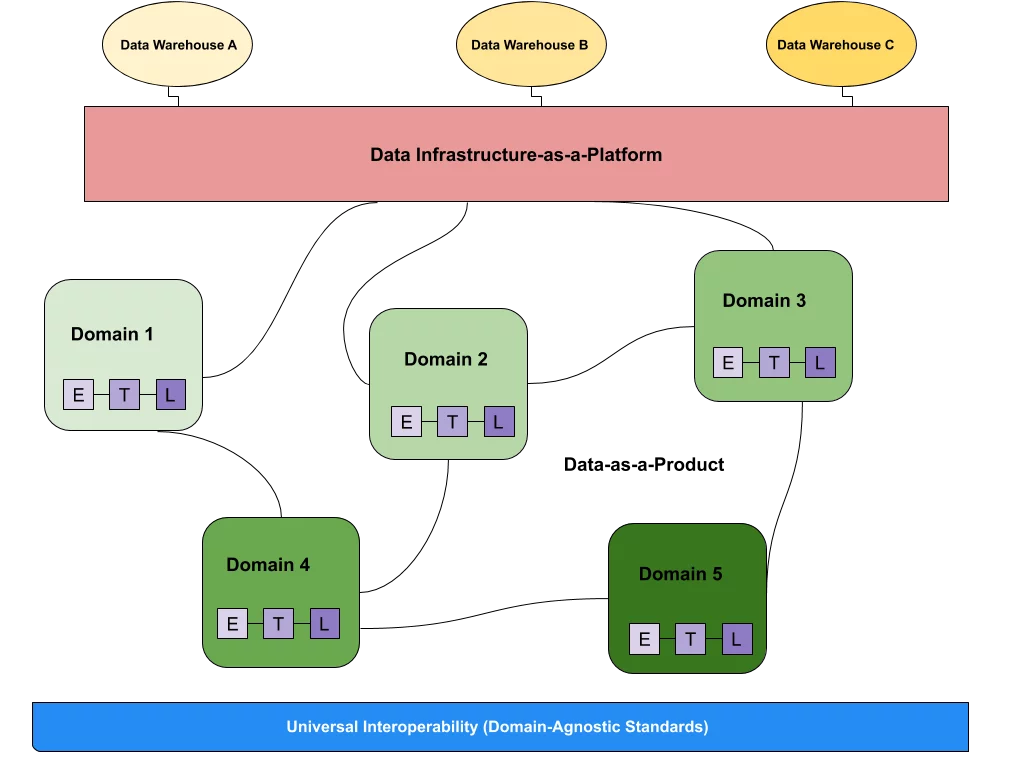 What is a data mesh--and how not to mesh it up
What is a data mesh--and how not to mesh it up 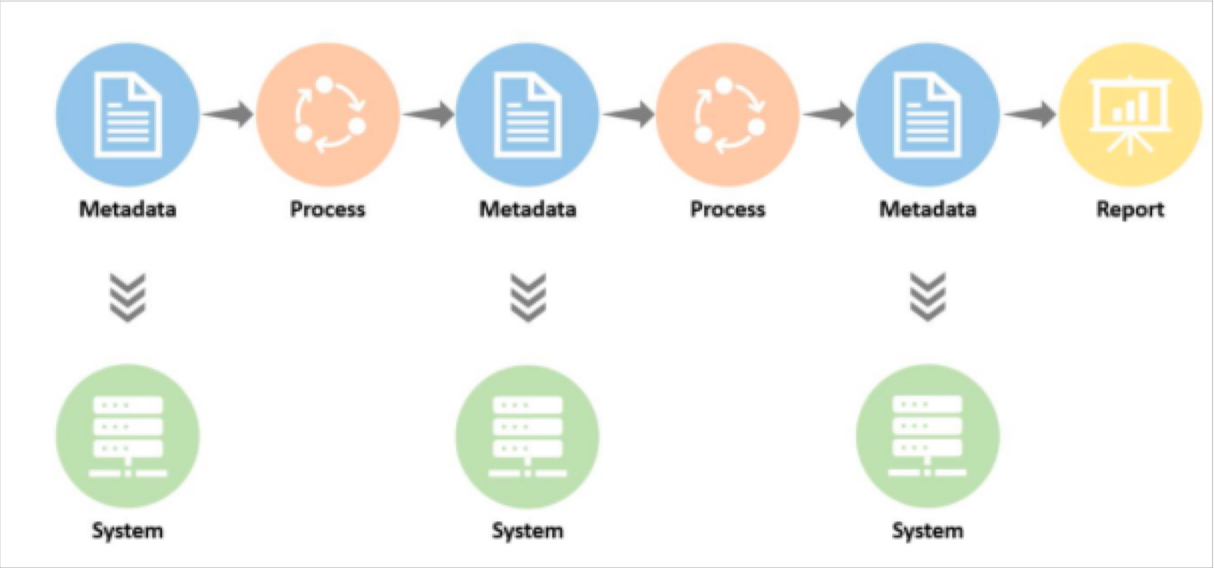 The ULTIMATE Guide To Data Lineage
The ULTIMATE Guide To Data Lineage